Target’s breach has created security concerns for businesses; and with each additional retailer that was breached following the Target incident (we know of at least six more), those concerns sore even higher. Here are at least five security takeaways from Target’s breach incident for CEOs, CIOs and any business executive that doesn’t want to be the next big breach story.
- Security Assessments
Security assessments solely focused on compliance is too limited in scope. There are a number of security assessments and they are not all the same. In order for yours to stop missing the mark, like in the case of Target, you need to development a holistic information security program. A 360 degree view is always better than a 180 degree view, isn’t it? And when what’s at risk is sensitive data (yours and your client’s), the stakes couldn’t be higher. - Compliance
You may have heard this already, but just in case you haven’t: compliance is the first step to a good security posture, but by no means the last and only step. There is no silver bullet to security, for as much as executives and security professionals wish there was. Compliance enforces you to set up the basic needs to start strengthening your security system, but it can’t make you proactive. A rule book tells you what you can or can’t do, but it doesn’t require you to be active 24/7 does it? And do you think malicious intruders follow a rule book, then sit back and wait before they attack? Or are they actively searching for their next target? - Brand Trust
The repercussions on brand trust take place from the outside, but also the inside. Executives and their CIOs are double checking and doubting every security system in place. After all, we are our worst critics when mishaps happen; not to mention how bad falling short on security is for business. As for the outside, customers are in doubt regarding every purchase they may want to make; wondering if their sensitive data will be safe or if they are at risk; and the news doesn’t help. A perfect example, Target’s CFO is set to testify before the Senate on the big data breach in February 2014, which further extends the correlation of breach and unsafe with Target, even though the breach occurred in November 2013. - Business Costs
If you think investing in an information security program is “costly,” think again. Breach costs are extremely high (Target losses could exceed $23.5 Billion). The 2013 Cost of Data Breach Study placed the average global cost of a data breach at $136 a record (2012) and for the United States the average data breach cost per record was placed at $188 (2012). To give you a better idea, here’s what the average total organizational cost of data breach looks like.
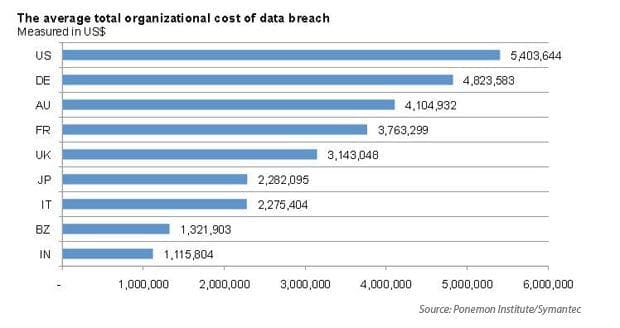 In addition to breaches being costly for business, research has shown that for the longest time security programs are seriously underfunded. In fact a recent survey shows that 62% of CIOs have said they do not have enough resources to effectively ward off security threats. Ergo, business costs decrease if enterprises invest in an effective information security program, not the other way around.
In addition to breaches being costly for business, research has shown that for the longest time security programs are seriously underfunded. In fact a recent survey shows that 62% of CIOs have said they do not have enough resources to effectively ward off security threats. Ergo, business costs decrease if enterprises invest in an effective information security program, not the other way around.
5. Surprises
When Target got breached, nobody thought healthcare would be affected; don’t you love a good surprise? Probably, not this surprise. It turns out that healthcare data stored in pharmacy records, such as Target’s, may be a prime target for thieves. If credit card protection was inadequate, why would it be different for EHI? It won’t. Surprises are ever present when dealing with data thieves and malicious intruders. This is another perfect example of why a well-rounded, 360 degree, holistic information security program is necessary if businesses wish to prevent havoc.
A good defense system doesn’t leave much room for blind spots. It doesn’t stop at the rule book; it doesn’t stop at the tools; and it doesn’t stop at the physical layout. No, it doesn’t; an effective information security program brings all the necessary components together.
How are you ensuring your information security posture is at 360 degrees to avoid blind spots?

